#126

Failure is often perceived as a setback, a blemish on an otherwise flawless record. However, in the realm of safety management, failure can be a potent tool for progress—if we are willing to embrace it.
Cultural Shift: From Fear to Freedom: In the pursuit of a safer workplace, fostering a culture that encourages the freedom to fail is paramount. This cultural shift is not about promoting failure but rather about creating an environment where reporting failures is encouraged without fear of retribution.
Risk Assessment and Preparedness: Vulnerability analysis stands as a pivotal tool in forecasting failure. Identifying vulnerabilities within the safety framework enables proactive measures to prevent potential mishaps. It’s not just about reacting to failures but preemptively planning to mitigate their impact.
Post 9/11 world, the concept of Vulnerability Analysis to predict failures.
Following the tragic events of September 11, 2001, the United States experienced a paradigm shift in its approach to national security, which included a significant focus on critical infrastructure protection. The Department of Homeland Security (DHS) was established in response to the 9/11 attacks to coordinate efforts aimed at securing the nation against various threats, including terrorism.
One crucial aspect of DHS’s mandate was to safeguard critical infrastructure, including sectors such as transportation, energy, water, and chemical facilities, among others, from potential terrorist attacks. Vulnerability analysis became a mandatory tool post-9/11 as part of DHS initiatives for several reasons:
-
Focus on Infrastructure Security: The 9/11 attacks highlighted the vulnerability of critical infrastructure to terrorist threats. DHS recognized the need to identify and address weaknesses within these infrastructures to prevent similar attacks or disruptions in the future.
-
Risk Assessment and Mitigation: Vulnerability analysis was seen as an essential component of risk assessment and mitigation strategies. By conducting comprehensive vulnerability analyses, DHS aimed to identify weaknesses and implement measures to reduce the likelihood of successful attacks on critical infrastructure.
-
Legislation and Mandates: The Homeland Security Act of 2002 empowered DHS to develop and implement programs to protect critical infrastructure. The act required DHS to conduct risk assessments and establish measures to mitigate vulnerabilities across various sectors, making vulnerability analysis a mandatory part of this process.
-
Public-Private Partnerships: DHS worked closely with private sector entities responsible for critical infrastructure to ensure their preparedness and resilience against potential threats. Vulnerability analysis was incorporated into collaborative efforts between government agencies and private industry to enhance security measures.
-
Regulatory Frameworks: DHS, in collaboration with other federal agencies, developed regulations, guidelines, and frameworks that required industries to conduct vulnerability assessments and implement risk-based security measures to protect critical infrastructure.
Overall, vulnerability analysis became a mandatory tool post-9/11 as part of a concerted effort by DHS to enhance the security posture of critical infrastructure, mitigate potential risks, and fortify the nation’s defenses against evolving threats, particularly in the context of homeland security and counterterrorism measures.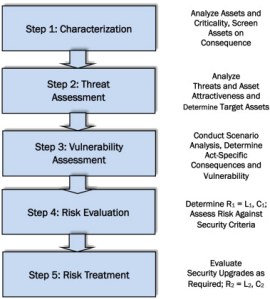
Vulnerability analysis involves a systematic examination of various factors that could leave an organization, system, or process exposed to risks and potential failures. Here are the key elements typically involved in vulnerability analysis:
- Asset Identification: Identifying and cataloging assets within an organization that are critical to its operations. This includes physical assets like infrastructure, equipment, and facilities, as well as intangible assets like data and information systems.
- Threat Assessment: Evaluating potential threats that could exploit vulnerabilities. These threats could be natural (such as earthquakes or floods), technological (cyber-attacks or system failures), or human-induced (sabotage, errors, or accidents).
- Vulnerability Identification: Analyzing weaknesses or vulnerabilities in assets or processes that could be exploited by identified threats. This includes understanding the weaknesses in security protocols, outdated technology, inadequate training, or insufficient maintenance procedures.
- Risk Analysis: Assessing the likelihood and potential impact of identified threats exploiting vulnerabilities. This step involves quantifying the risk level associated with each vulnerability to prioritize mitigation efforts effectively.
- Mitigation Strategies: Developing and implementing strategies to mitigate or reduce vulnerabilities. These strategies could include technological solutions, policy changes, training programs, redundancy in systems, or enhancing security measures.
- Monitoring and Review: Continuous monitoring of vulnerabilities and their associated risks is crucial. Regular reviews help in identifying new vulnerabilities that might emerge due to changes in technology, regulations, or operational practices.
- Response Planning: Establishing response plans to address vulnerabilities if they are exploited. This involves having protocols in place to react promptly and effectively in case a vulnerability is compromised.
- Documentation and Reporting: Maintaining comprehensive documentation of vulnerability analysis findings, mitigation strategies, and their implementation. This facilitates transparent communication within the organization and aids in regulatory compliance.
- Regular Updates and Adaptation: Recognizing that vulnerabilities evolve over time, it’s essential to continuously update and adapt vulnerability analysis processes to stay ahead of emerging threats and changing circumstances.
- Integration with Overall Risk Management: Integrating vulnerability analysis within the broader risk management framework ensures that it aligns with the organization’s overall risk strategy and objectives.
Vulnerability analysis is an ongoing and dynamic process that requires collaboration among different departments and stakeholders within an organization to effectively identify, assess, and mitigate risks and vulnerabilities that could lead to potential failures.
- Here’s a table comparing and contrasting vulnerability analysis and risk analysis:
| Aspect | Vulnerability Analysis | Risk Analysis |
|---|---|---|
| Focus | Primarily identifies weaknesses in assets or processes | Evaluates potential risks and their impacts |
| Definition | Identifies specific weaknesses that could be exploited | Analyzes potential threats and their likelihood |
| Scope | Concentrates on vulnerabilities within the system | Encompasses broader assessment of risks |
| Emphasis | Focuses on specific weaknesses and their exploitation | Considers the likelihood and impact of identified risks |
| Factors Considered | Weaknesses in assets, processes, or security measures | Threats, likelihood of occurrence, and potential impact |
| Outcome | Aims to address specific vulnerabilities identified | Aims to prioritize and manage risks effectively |
| Preventive Measures | Mitigates specific weaknesses to reduce exploitation | Develops strategies to manage and mitigate risks |
| Continuous Monitoring | Ongoing monitoring of vulnerabilities for updates | Constant monitoring of risks for adjustments |
| Relationship to Risk | A subset of risk analysis, focusing on vulnerabilities | Forms a part of risk analysis, assessing various elements |
| Depth of Assessment | Specific and detailed examination of identified weaknesses | Comprehensive assessment of risks across different facets |
| Example | Identifying a software vulnerability in an application | Assessing the risk of data breach due to cyber threats |
This comparison highlights the distinct aspects of both vulnerability analysis and risk analysis, showcasing their unique focuses and how they contribute differently to an organization’s overall risk management strategy.
Further:
- Learning from Incidents: Incidents, though undesirable, offer invaluable insights. Conducting comprehensive post-incident analyses helps uncover root causes, allowing organizations to rectify underlying issues rather than merely treating symptoms.
- Adaptation and Improvement: History is replete with instances where failures have been the catalyst for innovation. From the aviation industry to healthcare, every significant advancement in safety protocols stemmed from learning and improving after failure.
- Transparent Communication: Open dialogue about failures within an organization fosters collective learning. It’s about sharing lessons learned, enabling others to avoid similar pitfalls and fostering a sense of camaraderie in the pursuit of safety.
- Training and Continuous Improvement: Continuous training programs serve as a cornerstone in minimizing risks and preventing failures. Keeping employees updated with the latest safety measures ensures preparedness in handling unforeseen circumstances.
- Leadership’s Role: Leadership sets the tone for how failures are perceived. When leaders demonstrate that failures are not punitive but instructive, it encourages a culture of honesty and accountability.
- Regulatory Compliance and Innovation: Integrating regulatory compliance into vulnerability analysis ensures adherence to standards while also encouraging innovative solutions to prevent failures.
- Measuring Success: Success in safety management is not solely about the absence of failures. It’s about how an organization learns from failures, adapts, and continually improves its safety protocols.
Application of Vulnerability Analysis in a typical Manufacturing plant (Chemical). In a chemical manufacturing facility, vulnerability analysis can be applied to various critical areas to identify weaknesses that could lead to potential risks. Here’s a list of areas where vulnerability analysis can be effectively implemented:

